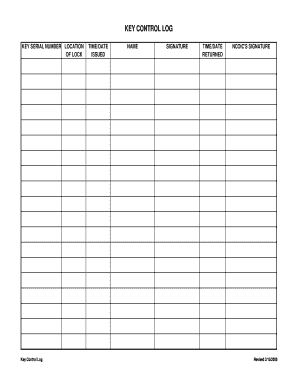
A printable key control log is a document used to track the movement and usage of keys within an organization. It helps to keep a record of who has access to specific keys, when they were checked out, and when they were returned. This log is an essential tool for maintaining security and accountability for keys, especially in settings where multiple people may have access to them.
By using a printable key control log, organizations can easily monitor and manage their keys, reducing the risk of loss or unauthorized access. It provides a clear record of key activities, making it easier to identify any discrepancies or issues that may arise.
Benefits of Using a Printable Key Control Log
There are several benefits to using a printable key control log in your organization. Firstly, it helps to improve security by ensuring that only authorized individuals have access to keys. By keeping track of who has checked out keys and when they were returned, you can quickly identify any potential security breaches.
Additionally, a key control log can help to streamline key management processes, making it easier to track and locate keys when needed. This can save time and effort for employees who are responsible for managing keys, as well as reduce the risk of keys being lost or misplaced.
How to Create a Printable Key Control Log
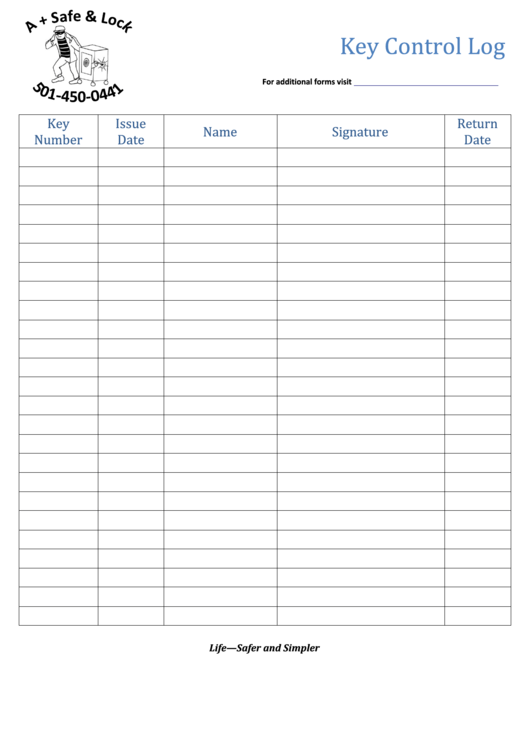
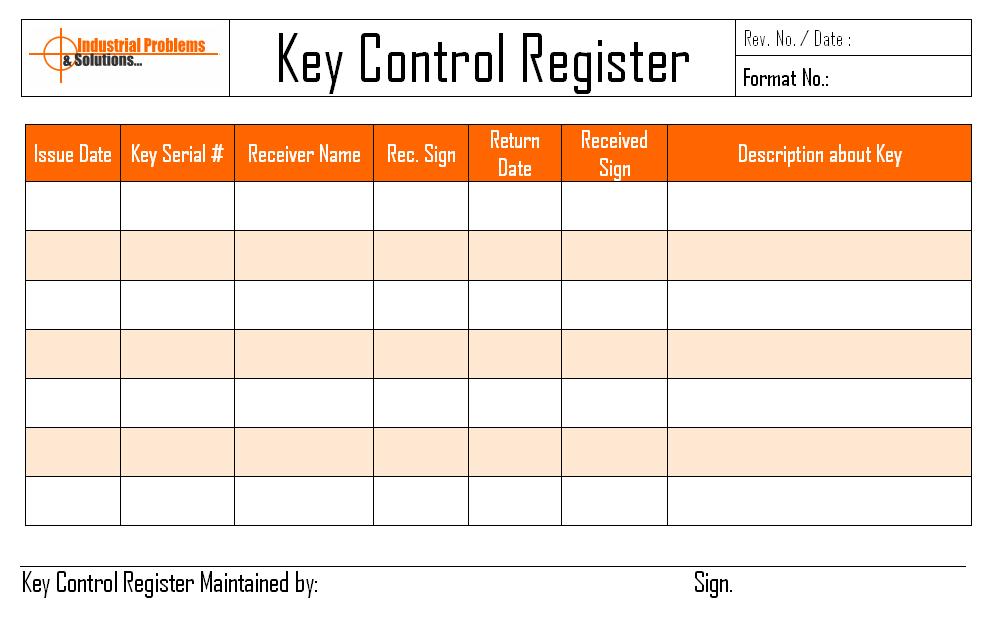
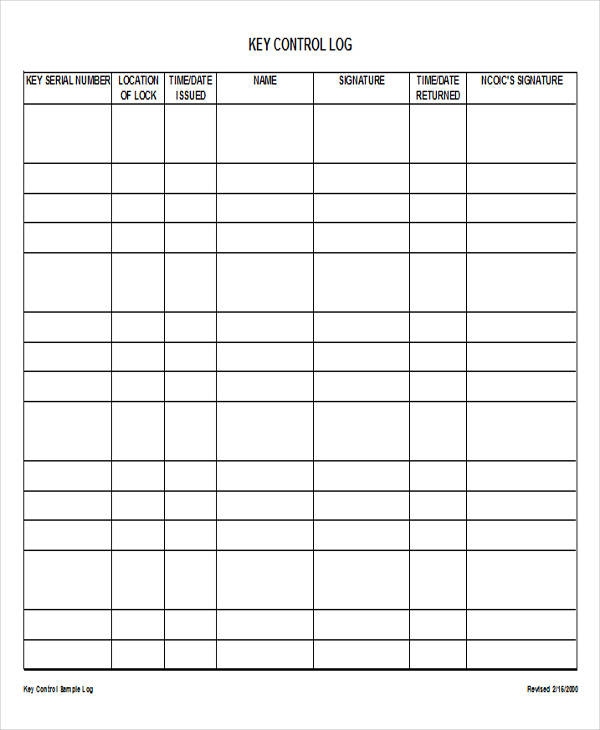
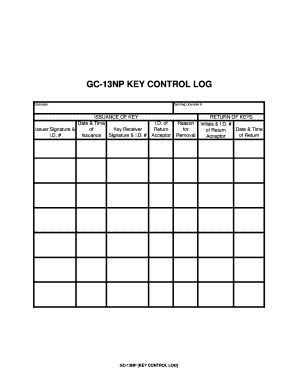
To create a printable key control log, you can use a template or design your own custom log using a word processing or spreadsheet program. Include columns for key details such as key number, description, location, date checked out, date returned, and the name of the individual checking out the key.
Make sure to regularly update the log as keys are checked in and out, and keep it in a secure location to prevent unauthorized access. By implementing a printable key control log in your organization, you can enhance security, improve key management processes, and ensure accountability for key usage.
By following these steps and utilizing a printable key control log, organizations can effectively manage their keys and enhance security measures within their premises.